Configuring Encrypted Communication Between HiveServer2 and Client Drivers
Unlike TLS/SSL, SASL QOP encryption does not require certificates and is aimed at protecting core Hadoop RPC communications. However, SASL QOP may have performance issues when handling large amounts of data, so depending on your usage patterns, TLS/SSL may be a better choice. See the following topics for details about configuring HiveServer2 services and clients for TLS/SSL and SASL QOP encryption.
Continue reading:
Configuring TLS/SSL Encryption for HiveServer2
HiveServer2 can be configured to support TLS/SSL connections from JDBC/ODBC clients using the Cloudera Manager Admin Console (for clusters that run in the context of Cloudera Manager Server), or manually using the command line.
Requirements and Assumptions
$ sudo keytool -genkeypair -alias $(hostname -f)-server -keyalg RSA -keystore \ /opt/cloudera/security/pki/$(hostname -f)-server.jks -keysize 2048 -dname \ "CN=$(hostname -f),OU=dept-name-optional,O=company-name,L=city,ST=state,C=two-digit-nation" \ -storepass password -keypass password
See the appropriate How-To guide from the above list for more information.
Using Cloudera Manager to Enable TLS/SSL
- Log in to the Cloudera Manager Admin Console.
- Select .
- Click the Configuration tab.
- Select Hive (Service-Wide) for the Scope filter.
- Select Security for the Category filter. The TLS/SSL configuration options display.
- Enter values for your cluster as follows:
For example:
Property Description Enable TLS/SSL for HiveServer2 Click the checkbox to enable encrypted client-server communications between HiveServer2 and its clients using TLS/SSL. HiveServer2 TLS/SSL Server JKS Keystore File Location Enter the path to the Java keystore on the host system. For example: /opt/cloudera/security/pki/server-name-server.jks
HiveServer2 TLS/SSL Server JKS Keystore File Password Enter the password for the keystore that was passed at the Java keytool command-line when the key and keystore were created. As detailed in How To Obtain and Deploy Keys and Certificates for TLS/SSL, the password for the keystore must be the same as the password for the key. HiveServer2 TLS/SSL Certificate Trust Store File Enter the path to the Java trust store on the host system. Cloudera clusters are typically configured to use the alternative trust store, jssecacerts, set up at $JAVA_HOME/jre/lib/security/jssecacerts.
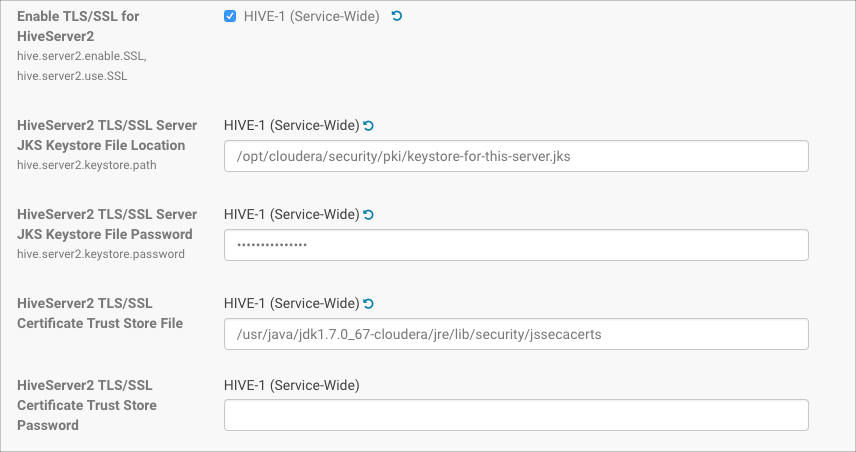
The entry field for certificate trust store password has been left empty because the trust store is typically not password protected—it contains no keys, only publicly available certificates that help establish the chain of trust during the TLS/SSL handshake. In addition, reading the trust store does not require the password. - Click Save Changes.
- Restart the Hive service.
Using the Command Line to Enable TLS/SSL
<property> <name>hive.server2.use.SSL</name> <value>true</value> </property> <property> <name>hive.server2.keystore.path</name> <value>/opt/cloudera/security/pki/keystore-for-this-server.jks</value> </property> <property> <name>hive.server2.keystore.password</name> <value>password</value> </property>
Client Connections to HiveServer2 Over TLS/SSL
Clients connecting to a HiveServer2 over TLS/SSL must be able to access the trust store on the HiveServer2 host system. The trust store contains intermediate and other certificates that the client uses to establish a chain of trust and verify server certificate authenticity. The trust store is typically not password protected.
 Note: The trust store may have been password protected to prevent its contents from being modified.
However, password protected trust stores can be read from without using the password.
Note: The trust store may have been password protected to prevent its contents from being modified.
However, password protected trust stores can be read from without using the password.- Pass the path to the trust store each time you connect to HiveServer in the JDBC connection string:
jdbc:hive2://fqdn.example.com:10000/default;ssl=true;\ sslTrustStore=$JAVA_HOME/jre/lib/security/jssecacerts;trustStorePassword=extraneous
or, - Set the path to the trust store one time in the Java system javax.net.ssl.trustStore property:
java -Djavax.net.ssl.trustStore=/usr/java/jdk1.7.0_67-cloudera/jre/lib/security/jssecacerts \ -Djavax.net.ssl.trustStorePassword=extraneous MyClass \ jdbc:hive2://fqdn.example.com:10000/default;ssl=true
Configuring SASL Encryption for HiveServer2
| auth | Default. Authentication only. |
| auth-int | Authentication with integrity protection. Signed message digests (checksums) verify the integrity of messages sent between client and server. |
| auth-conf | Authentication with confidentiality (transport-layer encryption). Use this setting for encrypted communications from clients to HiveServer2. |
<property> <name>hive.server2.thrift.sasl.qop</name> <value>auth-conf</value> </property>
Client Connections to HiveServer2 Using SASL
beeline> !connect jdbc:hive2://fqdn.example.com:10000/default; \ principal=hive/_HOST@EXAMPLE.COM;sasl.qop=auth-confThe _HOST is a wildcard placeholder that gets automatically replaced with the fully qualified domain name (FQDN) of the server running the HiveServer2 daemon process.
| << Configuring TLS/SSL for Flume Thrift Source and Sink | ©2016 Cloudera, Inc. All rights reserved | Configuring TLS/SSL for Hue >> |
| Terms and Conditions Privacy Policy |